You should install this Chrome update now
last friday, google Release of an unplanned new security update that addresses a very serious vulnerability in Chrom Which, according to the company, is currently actively exploited.
Track K CVE-2022-1096, the zero-day defect is related to the type of vulnerability to confusion in the V8 JavaScript engine. An anonymous researcher was credited with reporting the error on March 23, 2022.
Confusion errors, which appear when accessing a resource (for example, a variable or object) with a type that is incompatible with the type originally initialized, can have serious consequences in non-memory-safe languages, such as C and C++. , allowing a malicious user to break out of memory access limits.
The tech giant acknowledged that it was “aware of an exploit for CVE-2022-1096,” but did not share additional details to prevent further exploits, and so most users are using this new version of Chrome.
CVE-2022-1096 is a zero-day vulnerability that Google has been addressing in Chrome since the beginning of the year, the first of which is CVE-2022-0609, a security vulnerability use after free In the animation element that was fixed on February 14th.
Earlier this weekGoogle’s Threat Analysis Group (TAG) has released details of a dual campaign by North Korean groups that are using the flaw to target US-based organizations that include the media, information technology, cryptocurrency and financial technology industries.
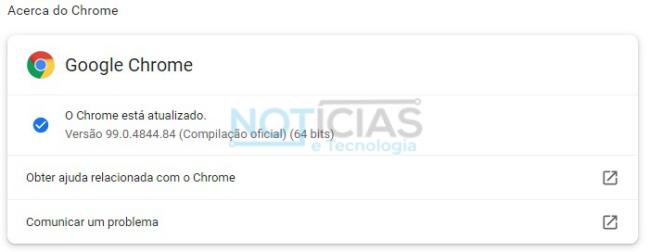
Google Chrome users are highly recommended to update to the latest version, which now contains version 99.0.4844.84 on Windows, Mac, and Linux.
You have already left your like on our page on Facebook? Get all the information directly. Also follow us on Google News, just choose us from your favorites by clicking on the star.

Founder of Noticias e Tecnologia, and this is his second online project, after several years associated with an Android-focused portal, of which he was also one of the founders.
Computer worker by profession, passionate about new technologies, motorsports and mountain biking.

“Coffee trailblazer. Social media ninja. Unapologetic web guru. Friendly music fan. Alcohol fanatic.”

